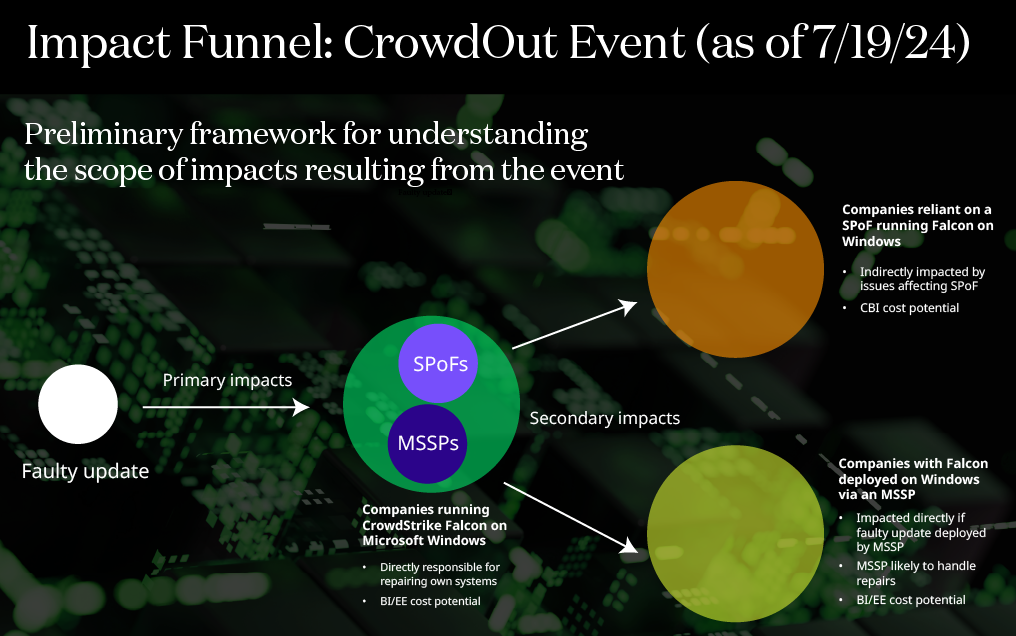
The faulty CrowdStrike Falcon Sensor update and subsequent outage underscore the potential for single point of failure technology outages to impact the global digital economy, according to cyber risk analytics specialists at CyberCube.
Analysis of the companies exposed across CyberCube’s US Industry Exposure Database identifies large companies in manufacturing, IT, healthcare and the financial sector as the most likely to be exposed. Examination of exposed limits shows an outsize exposure in the aviation, banking and retail sectors. CyberCube is advising clients on how to use SPoF Intelligence to identify exposed insureds and estimate the exposure footprint of the event.
The faulty update affects companies using CrowdStrike’s Falcon software on machines running Windows OS, both desktop (including Windows 10 and 11) and Windows Server. Given its global position in cyber security, CrowdStrike’s own customer base includes many other organisations that CyberCube identifies as SPoFs. Companies relying on one of these SPoFs may be secondary victims of the event, even if they do not use CrowdStrike and Windows directly.
Additionally, CrowdStrike Falcon is deployed by managed security service providers on the networks of other – typically smaller – organisations they oversee, according to the cyber specialist. These organisations using such MSSPs are also secondary victims of the event. Notably, financial institutions, healthcare providers and transportation networks have all experienced disruptions.
Applying CyberCube's own SPoF Intelligence tool to search for insureds that are dependent on CrowdStrike Falcon shows it is likely that all users of the core components of the CrowdStrike Falcon platform in conjunction with Windows OS are impacted. CyberCube has provided clients with a list of SPoFs that are dependent both on CrowdStrike Falcon and Windows OS. The outage affects various versions of Windows operating systems. This broad scope means that any organisation or individual using these operating systems alongside CrowdStrike Falcon is at risk of experiencing system crashes and operational disruptions.
The primary impacts of the incident closely resemble two scenarios in CyberCube’s Portfolio Manager aggregation model, it said: modelling scenario classes 41 (operating system disruptions on endpoints) and 42 (operating system disruptions on servers) within CyberCube’s event catalogue show the incident to be mainly a system failure or business interruption event.
Secondary impacts by way of additional SPoFs that fall within this primary footprint may also be expected. SPoFs for scenario classes 4, 9, 10, 11 and 18 (mainly related to financial services and payment system technologies) have been observed as users of CrowdStrike and Windows operating systems, exposing companies that rely on these SPoFs to possible contingent business interruption outages.
Affected organisations can expect a series of remediation and recovery efforts to take place immediately. Companies with the IT resources to handle large-scale incidents are expected to recover faster. There may be ongoing disruptions as companies implement patches and verify their systems' stability. Rolling back the update and applying patches requires specialist knowledge. SMEs, and companies lacking robust contingency or IT back-up plans are likely to face additional disruptions.
CyberCube's Cyber Aggregation Event Response Service has been activated as a result of the CrowdStrike event. CAERS provides up-to-date intelligence on major cyber catastrophes worldwide as they unfold.
Last week’s global IT system outage was triggered by a faulty software update from CrowdStrike, causing widespread disruptions across various Windows operating system types. The issue originated from a defective kernel driver included in the update, which led to numerous systems crashing globally and displaying the blue screen of death. The issue began with a CrowdStrike update that was intended to enhance security but inadvertently included a logic error in a configuration file. Invalid operations caused by the logic error led to the OS encountering conditions it cannot resolve. This resulted in system crashes.
Infographic courtesy CyberCube
Printed Copy:
Would you also like to receive CIR Magazine in print?
Data Use:
We will also send you our free daily email newsletters and other relevant communications, which you can opt out of at any time. Thank you.









YOU MIGHT ALSO LIKE